













Network Security , Data Backup and Recovery, Access Control Systems and more

Surveillance Cameras,Access Control Systems, Inventory Tracking Solutions, and more

Campus Surveillance, Access Control Systems, Visitor Management Systems and more

CCTV Cameras, Access Control Systems, Biometric Authentication Firewalls and Encryption and more

Surveillance Cameras,Access Control Systems, Patient Monitoring Systems, and more


Remote access and control of building systems for real-time management and optimization and more

Verification of intrusion alarms with video surveillance footage for enhanced security response and more

IP surveillance cameras are digital cameras that use Internet Protocol to transmit image data and control signals over a network, offering remote viewing and higher resolution than traditional CCTV.

CCTV cameras are security devices that capture and record video footage of surroundings to monitor activities, deter crime, and provide evidence in case of security breaches.

Cameras equipped with sensors that switch between color during the day and black and white at night for enhanced low-light performance.

These cameras offer remote control over pan, tilt, and zoom functions, allowing operators to monitor larger areas and track subjects with precision

Cameras that connect to the network wirelessly, providing flexibility in installation and reducing the need for extensive cabling.

Cameras that detect heat signatures detecting intruders in complete darkness or adverse weather conditions.
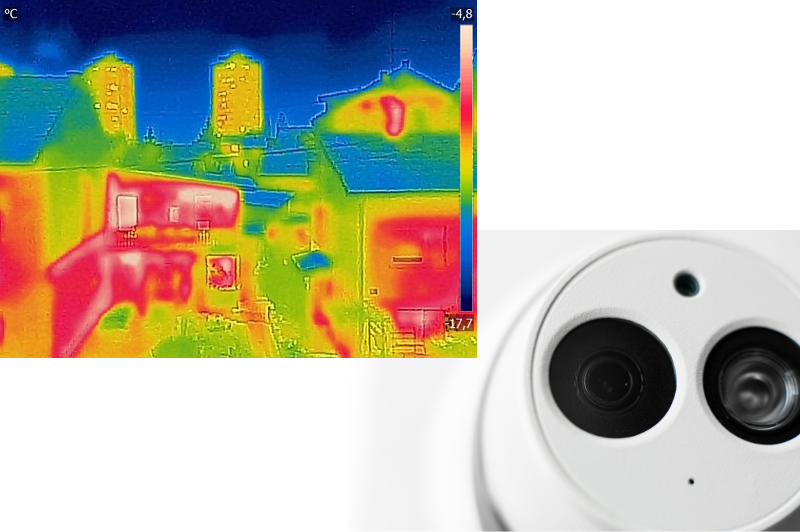
Cameras with built-in infrared LEDs to capture clear images in low-light or complete darkness. They are commonly used for nighttime surveillance

Users gain access using proximity cards, smart cards, or magnetic stripe cards. These cards are swiped or tapped on a reader to grant access.

It involves capturing and analyzing the unique patterns present in an individual’s fingerprint for authentication.

It’s commonly used in access control systems and surveillance applications.

Aaccess control decisions are made by controllers installed at each door

This ensures that access is only granted during specific hours or days of the week.

They may include features such as visitor registration, badge printing, and temporary access permissions.

These systems use biometric identifiers such as fingerprints, iris patterns, or facial recognition to verify a person’s identity before granting access.

Users enter a unique PIN or code on a keypad to gain access. This method is commonly used in conjunction with other access control methods for added security.

Keyless entry systems use wireless technology, such as Bluetooth or RFID, to grant access via smartphones, key fobs, or wearable devices.

These cards offer enhanced security features compared to traditional magnetic stripe cards.

These systems control access to parking lots, garages, or gated areas for vehicles. They may use RFID tags, license plate recognition, or proximity sensors for vehicle identification.

Remote access control systems allow users to grant or revoke access permissions remotely, typically through a web-based interface or mobile app. This is useful for managing access to multiple locations or remote sites

Wireless access control systems eliminate the need for extensive wiring between doors and controllers

Multi-door access control systems can incorporate biometric authentication methods for enhanced security and used to verify the identity of users at each access point.












We take up Interior Work and setting up Modular Work Station along with other IT Infrastructure and security Solutions for new and renovating offices.
Ready to take your business to the next level with our technology solutions? Fill out the form to connect with us and explore exciting opportunities for collaborations
+917899497979
#131 Richi Complex, 1st Floor, 4th Cross, Chinnappa Layout, kammannahalli, Bangalore 560084
Monday -Saturday 9:00 am - 6:00 pm
© 2024 Created with Yateer Creative Solutions